Quibi has changed its signup process in response to allegations that it shared users’ email addresses with a range of third-party organizations, including advertising and analytics sectors of Google, Facebook, Snapchat, and Twitter.
According to an April 29 report from Zach Edwards, founder of analytics consulting firm Victory Medium, when a new Quibi user signed up for an account and confirmed their email address, that address was automatically being shared without users’ knowledge or consent.
That’s because of the type of code the confirmation page was running, Edwards explained. “When a user loads a webpage, the URL that they are visiting, along with any URL parameters (extra tracking codes appended after a ‘?’ in a URL) are shared with any advertising or analytics companies through the JavaScript code on that page,” he wrote.

Subscribe for daily Tubefilter Top Stories
Data is also shared through a common analytics tool known as an HTTP referer. When you browse the internet and click on the a link, the referer embedded in that link sends a request–and information about you, like geographical location–to the server that hosts the webpage you’re trying to visit. In some cases, though, that outgoing ping can go not only to the host server, but to third parties.
That’s what happened with Quibi, Edwards alleges. He took the URL a user would be served after they confirmed their email address, and picked apart its JavaScript. Doing so showed that Google, Facebook, Snapchat, Twitter, and management consulting company CivicComputing.com all got users’ email addresses from the confirmation link’s HTTP referer.
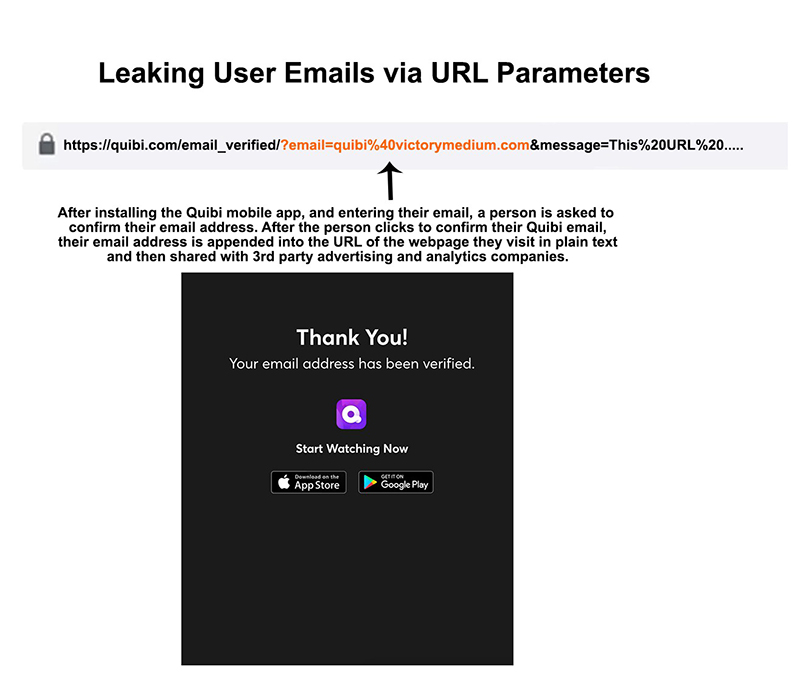
credit: Zach Edwards
They (and Quibi) could then use those addresses to track users’ activity across the web, collecting more information all the while. The practice is “a sloppy and dangerous growth hack that is used to improve attribution tracking for analytics tools and used to optimize and segment retargeting advertising campaigns,” Edwards alleges.
This leak appears to have only affected users who confirmed their email addresses using Google Chrome, as rival browsers like Safari and Firefox all use JavaScript and cookie blocking features by default, Edwards said.
He acknowledged that these kind of data leaks can happen accidentally, but alleged that “it’s an extremely disrespectful decision to purposefully leak all new user emails to your advertising partners, and there’s almost no way that numerous people at Quibi were not only aware of this plan, but helped to architect this user data breach.”
Edwards says he informed Quibi of the data privacy concerns on April 17, and that as of April 26, nothing about the service’s JavaScript had been changed.
Quibi disagrees on both counts. It was unaware of the leak despite rigorous engineering and security testing, it tells Tubefilter, and was not informed about issues until April 28. “The moment the issue on our webpage was revealed to our security and engineering team, we fixed it immediately,” a spokesperson says.
When we tested the fix by signing up for a new Quibi account and confirming the email we gave, the confirmation page did not have the JavaScript Edwards called attention to. Following the confirmation link from a computer now leads to an otherwise blank page that says, “Thank You! Your email address has been verified.” Following it from a phone confirms the address, then automatically reopens the Quibi app.
Edwards’ research identified a number of other organizations with similar JavaScript data breaches, including ecommerce site Wish, marketing platform Mailchimp, and The Washington Post. Collectively, compromised organizations have leaked “hundreds of millions” of emails, Edwards said. Wish, Mailchimp, and the Post all changed their email setups within 72 hours of being notified, but “many other organizations either didn’t respond or have failed to take any actions for weeks or months,” he said.
He concludes that companies like Quibi should publicly post the names of all advertising and analytics vendors that could’ve received their users’ email addresses. They should also issue deletion requests to those vendors, and ensure their processes are not sending data–accidentally or on purpose–to third parties.